Internal auditors have a lot on their plate. As the primary party responsible for keeping their organization’s financial controls stable, strong, and comprehensive, they play a significant role in ensuring compliance. They work on the organization’s behalf, finding areas of improvement, communicating with stakeholders, managing risk and detecting fraud. One of the ways they do this is by building an effective audit trail. This blog post will introduce the concept of an audit trail, and some internal control best practices to keep it robust and referenceable.
Table of Contents
What Is an Audit Trail?
An audit trail, sometimes called an audit log, is a bit of a metaphorical “snapshot” of financial data surrounding a particular record, user, or transaction. AccountancyAge describes it as “a sequence of documents that evidences the progress of a transaction from its inception to completion“. They are frequently mandated, essential for transparency, and always a best practice. They range quite substantially in complexity, from simple details to needing technical expertise to understand and act upon.

But as auditors already know, hurdles and difficulties exist with maintaining effective and comprehensive audit trails.
Complexities and Difficulties
Commonly cited complexities and difficulties with maintaining a good audit trail can be largely attributed to three main categories.
Limited resources
This encompasses issues related to cost and budget, as well as organizational or personnel resource limitations. It comes down to the fact that large organizations may have trouble keeping up with the sheer volume of data. It’s an issue we’ve come across repeatedly talking to professionals across industries, so if this describes you, you’re not alone.
Data security
Keeping data private and safe is of utmost concern to organizations with strong internal auditing processes. As cybercrime remains a significant threat, a strong audit trail is one line of defense against outside attacks.
The human element
Even with the advent of AI and machine learning, there still exists significant manual processes in all assets of accounting, procurement, and financial services. Where there exist manual processes, there exists potential for incomplete or inaccurate audit trails.
Internal Control Best Practices: Data Review
We’ve compiled some best practices to keep in mind while auditing your organization’s spend data, including Accounts Payable (AP), general finance and accounting, and procurement/P-Card data.
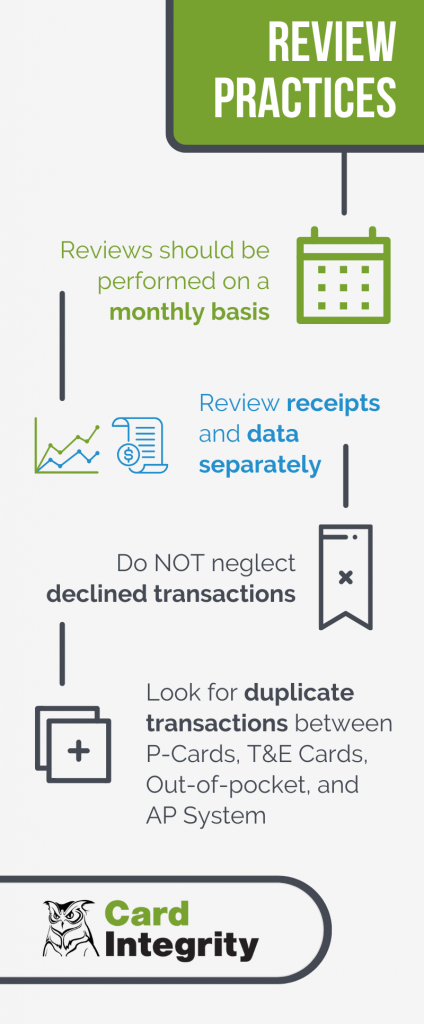
- Perform reviews on a monthly basis. A monthly expense review is imperative to your auditing efforts. This will provide a clear breakdown of the overall spend, giving you a bird’s eye view of where your data is doing.
- Review data and receipts separately. Match expense data to receipts by reviewing them separately. Receipts help validate that approved purchases were made in approved amounts from contracted suppliers.
- Don’t neglect declined transactions. Declined transactions indicate that the card user either tried to exceed their spending limit or knowingly or unknowingly violated another policy. While it’s nice to know that declined transactions provide a safeguard for compliance, this is also a great opportunity to communicate with the cardholders and reiterate, or train on, card policy standards so that they can learn for the future.
- Lastly, look for duplicate transactions between P-Cards, T&E Cards, out-of-pocket purchases, and the AP system. Duplicate payments waste money and are often a red flag for deeper issues. Luckily, the solution provides an easy fix to limit risk in this area. Examining declined transactions and potential duplicate transactions are key ways to achieve compliance and generate more cost savings.
Internal Control Best Practices: Fraud and Abuse
It goes without saying that preventing fraud and abuse is of utmost concern to your organization. Increasing spend visibility with a data system that aggregates findings and trends will be your key to financial audit success.
Uncover Level III Data
One way that data can help catch and prevent fraud is by revealing Level III transaction information. Level III data includes line-item details about a credit card purchase whether it’s the actual item code, quantity, supplier, and other information.
Unfortunately, receipts can be fabricated and purchase values don’t always tell the whole story. Accessing Level III is just one other meaningful way to connect the dots and tighten up your spend controls to prevent card misuse and fraud.
Cancel and Retrieve Commercial Cards
One way that organizations are defrauded is by former employees. Somehow, things slip through the cracks and they manage to retain access to a corporate card despite not working at the organization any longer. This could either be an innocent mistake, or the work of a vengeful employee. A thorough audit stops this type of fraud in its tracks before it has a chance to get started.
Establish Clear Management Responsibilities
Oftentimes, management in organizations that are responsible for reviewing financial data don’t have the proper level of accountability or oversight to do so. For example, problems can occur when a manager that is responsible for reviewing his or her employees’ P-Cards holds a P-Card themselves. Of course, not every instance where this is the case means fraud is happening, but it certainly creates risk. Organizations that have internal auditors in place are already ahead in this area.

Internal Control Best Practices: Communication
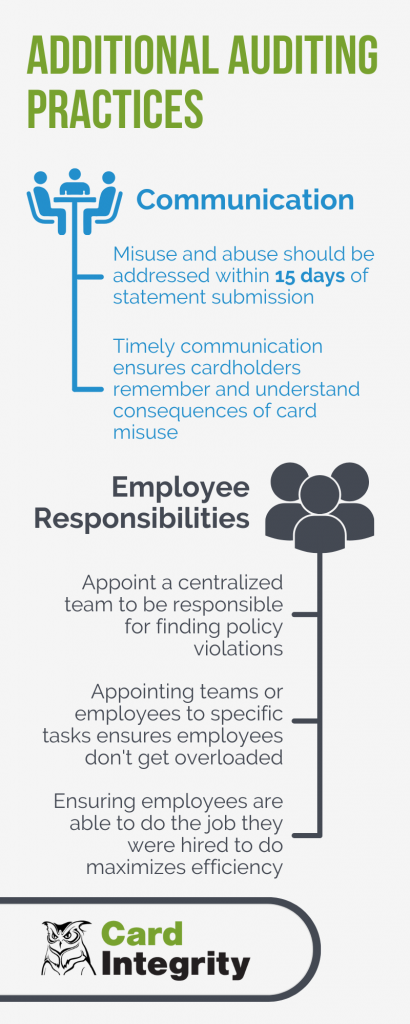
When auditors communicate with employees, they should address misuse and abuse as soon as possible. Additionally, timely communication ensures that they remember and understand the consequences of any policy violations, for example card misuse, gift card purchasing, split transactions, rogue spend, or duplicate payments.
Employee responsibilities are something that should be clear for all involved in your organization’s spend. Make responsibilities clear, which will maximize your program’s efficiency.
Join the Internal Audit Insights Mailing List
By keeping your internal controls effective and strong, you make your audit trails more useful and referenceable in the long run. Sign up below to gain access to curated best practices about internal controls and auditing from our library of content. This content is designed for internal auditors, procurement managers and accounts payable managers at government institutions, universities, and corporations in the public and private sectors.

